Download-Software etikettierte vorbei begginer computer user
|
Das populärste Programm: Quick Slide Show 2.00

mehr Info |
|
Wir empfehlen uns: Keylogger Software with Screen Capture 3.0.1.5
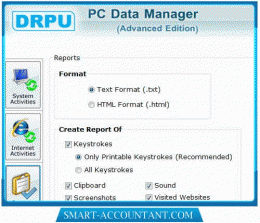
mehr Info |
Doorway Blaster 1.3.2 durch SPCK Software
2007-09-15
Generate doorway (lead in) pages that will create massive traffic to your site. These doorway pages will be registered and indexed on search engines. When an internet user does a search, your doorway pages will show up and lead them to your site!
Asee iPhone Transfer Photo 7.1.26.03 durch iPhoneSoftware.Inc.,
2007-10-29
iPhone Transfer Photo is an easy to use backup software that lets you copy photos from your iPhone to a Windows based PC with the least effort. Apple had integrated all your photos into an ithmb file which user can not access the content directly.
SearchRefiner 1.0 durch MadeForNet
2008-01-24
SearchRefiner delivers individual search results to each computer user based on his/her professional interests and hobbies. t refines the search results by moving the results that are more relevant to you to a higher position on the list.
US-State Anti-virus Adware Spyware Bot 1.4.19 durch Anti-virus Adware Spyware Bot
2008-01-27
US-State Anti-virus Adware Spyware Bot - The term rootkit is used to define a Trojan (or technology) used to hide the presence of a malicious object (process, file, registry key, network port) from the computer user or administrator.
Swift Anti Binder Keyloggers Spy 1.3.73 durch Anti Binder Keyloggers Spy
2008-08-10
Swift Anti Binder Keyloggers Spy - The term rootkit is used to define a Trojan (or technology) used to hide the presence of a malicious object (process, file, registry key, network port) from the computer user or administrator.
Swift Clean BHOs Binder Trojan Horses 1.1.11 durch Clean BHOs Binder Trojan Horses
2008-03-06
Swift Clean BHOs Binder Trojan Horses - The term rootkit is used to define a Trojan (or technology) used to hide the presence of a malicious object (process, file, registry key, network port) from the computer user or administrator.
Bliss Destroy Bot Binder Adware 1.5.86 durch Destroy Bot Binder Adware
2008-08-12
Bliss Destroy Bot Binder Adware - The term rootkit is used to define a Trojan (or technology) used to hide the presence of a malicious object (process, file, registry key, network port) from the computer user or administrator.
Bliss AntiSpyware RAT Spoofers Keyloggers 1.4.34 durch AntiSpyware RAT Spoofers Keyloggers
2008-08-12
Bliss AntiSpyware RAT Spoofers Keyloggers - The term rootkit is used to define a Trojan (or technology) used to hide the presence of a malicious object (process, file, registry key, network port) from the computer user or administrator.
Ever Discover Password Cracker Viking Hijackers 1.2.90 durch Discover Password Cracker Viking Hijackers
2008-02-26
Ever Discover Password Cracker Viking Hijackers - The term rootkit is used to define a Trojan (or technology) used to hide the presence of a malicious object (process, file, registry key, network port) from the computer user or administrator.



